What is Self Hosted OpsLevel
While OpsLevel's Software-as-a-Service offering will work best for most organizations, some organizations may prefer to host OpsLevel themselves. This guide will walk you through how OpsLevel provides the option to host OpsLevel themselves and a high level overview of the self hosted OpsLevel application architecture.
For more detailed instructions on configuring OpsLevel Self Hosted, see Getting Started with Self Hosted OpsLevel.
How it works
OpsLevel has partnered with Replicated to provide a superior installation & support experience for self-hosting a copy of the OpsLevel application.
OpsLevel's Application Architecture runs in a Kubernetes cluster and Replicated provides a configuration and admin experience to simplify distribution of new versions and configuration of the Application. Our configuration in Replicated will create several deployments for OpsLevel's Web Application, workers and runners. OpsLevel requires several additional infrastructure components, such as databases, queues and search clusters.
Many of OpsLevel's integrations involve push mechanisms from third party services, so your Self Hosted OpsLevel will need to be accessible to those services over the internet. See below for a visualization of the OpsLevel application's architecture.
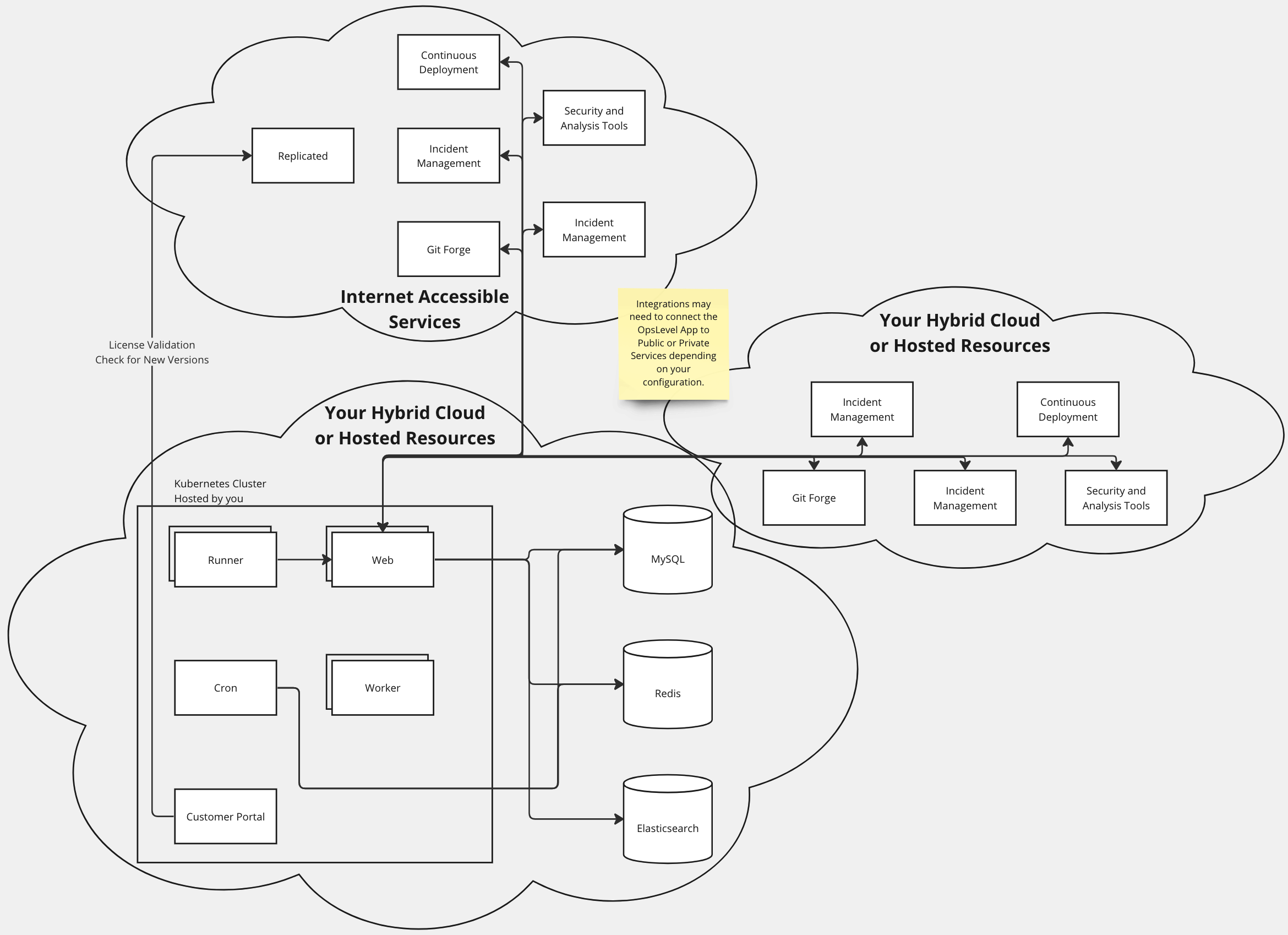
Application Architecture Diagram
Updated 2 months ago
Follow the guide to get your self hosted OpsLevel application up and running
