Snyk Integration
Integrate with Snyk to check for vulnerabilities for your services in OpsLevel.
Add a Snyk integration
1. In the OpsLevel app, Click Integrations in the left sidebar.
2. Click on the +New Integration button.
3. Click the Snyk tile to add the integration.
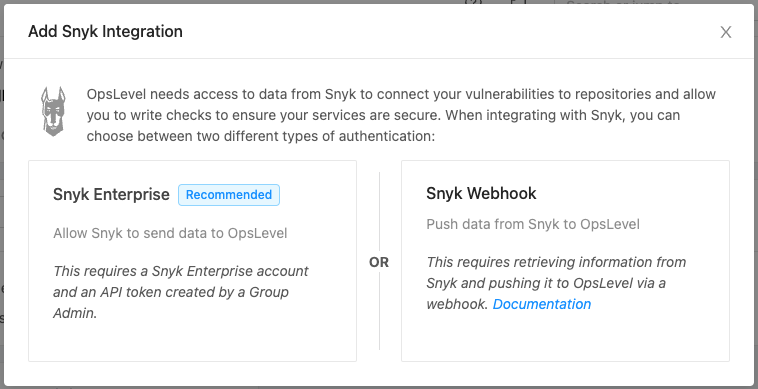
Snyk Enterprise
Our Snyk Enterprise integration automatically syncs data from Snyk into your catalog. This integration powers Code Issue checks and populates Code Issues and Code Issue Projects on your Repositories and Services.
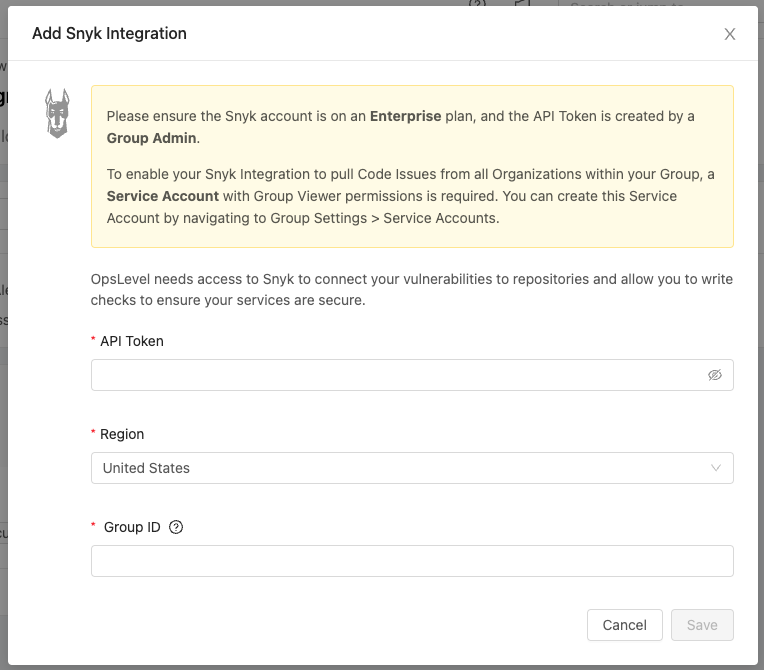
To set up this API-based integration, you need:
- A Service Account with Group Viewer permissions
- An API token associated with that Service Account (API token must be created by a Group Admin)
- Your Group ID and Region
Webhook integration (all Snyk tiers)
If you don't have a Snyk Enterprise account, you can use your Snyk data to power Custom Event Checks in OpsLevel. Use the Snyk Webhook config to push data to your checks - see instructions below.
Create a Code Issues check (Snyk Enterprise integration)
With the Snyk Enterprise integration, OpsLevel stores all code issues detected by Snyk, such as vulnerabilities and config issues, in your catalog. You can run checks against your code issues using a Code Issue Check.
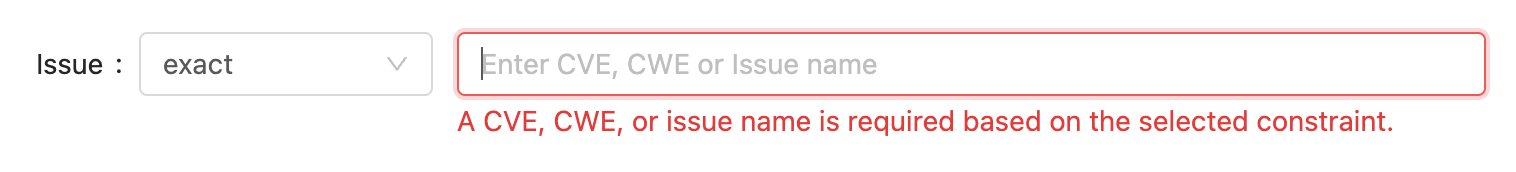
If you're checking for a specific CVE or CWE, you can search for an exact match on the issue identifier.
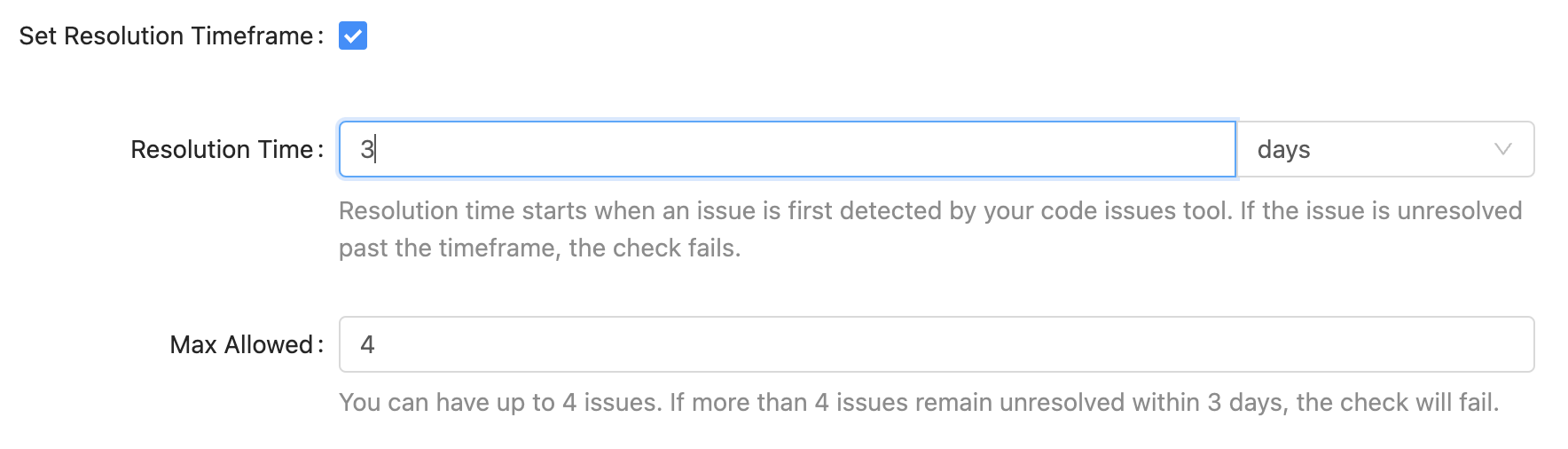
For all code issue checks, you can set a resolution timeframe, and a maximum allowable number of code issues. Your check will begin to fail if the time between a code issue being detected and the code issue being fixed exceeds that timeframe for more than the maximum allowable number of issues.
Create a Custom Event Check (webhook integration)
1. Navigate to the Rubrics sub menu under the Service Health menu in OpsLevel
2. Hover over the cell that corresponds to the level and category you want your check to live in and click the +Add Check button.
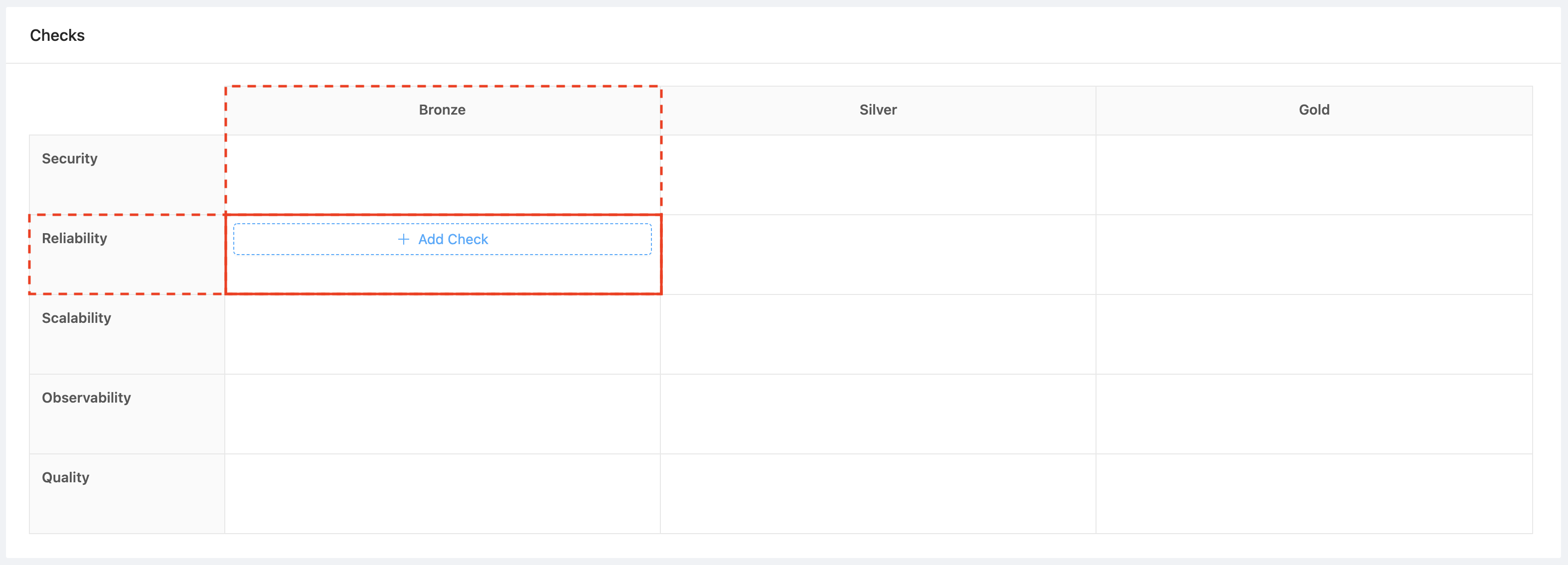
3. Create a Snyk check from the Integrations section
4. Choose one of the Check Templates from the Use a template to help build a Custom Event Check dropdown.

Here is what each template is for:
- No Critical Vulnerabilities: Any service that has critical vulnerabilities in its package manifest file will fail this check.
- No High Vulnerabilities: Any service that has high vulnerabilities in its package manifest file will fail this check.
- Less than 3 Medium Vulnerabilities: Any service with 3 or more medium vulnerabilities in its package manifest file will fail this check.
- Less than 5 Low Vulnerabilities: Any service with 5 or more low vulnerabilities in its package manifest file will fail this check.
5. We will populate the Service Specifier field, which we use to determine what service to run the check for, and the Success Condition field, which we use to determine if the check should pass or fail. We also provide a sample payload to test the check.

Send payload to OpsLevel
snyk test --prune-repeated-subdependencies --json |
curl -X POST https://app.opslevel.com/integrations/custom_event/xxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx \
-H 'content-type: application/json' --data-binary @-This will send all the vulnerabilities for the service to OpsLevel and we will execute the check that was created in the previous step. You will need to substitute the endpoint URL from the Snyk Integration you created in place of xxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx.
To learn more about the Snyk CLI, you can read their docs.
Updated 2 months ago
