SonarQube Integration
Integrate with SonarQube to check for vulnerabilities for your services in OpsLevel.
Our SonarQube integration automatically syncs data from SonarQube into your catalog. This integration powers Code Issue checks and populates Code Issues and Code Issue Projects on your Repositories and Services.
The SonarQube integration supports the most recent version (currently v10.7) and the “Long Term Active” version (v9.9) of the SonarQube software.
While we officially support only the latest versions, we have successfully tested the integration with multiple releases of both v9.x and v10.x.
Add a SonarQube Integration
- In the OpsLevel app, Click Integrations in the left sidebar.
- Click on the + New Integration button.
- Click the SonarQube tile to add the integration.
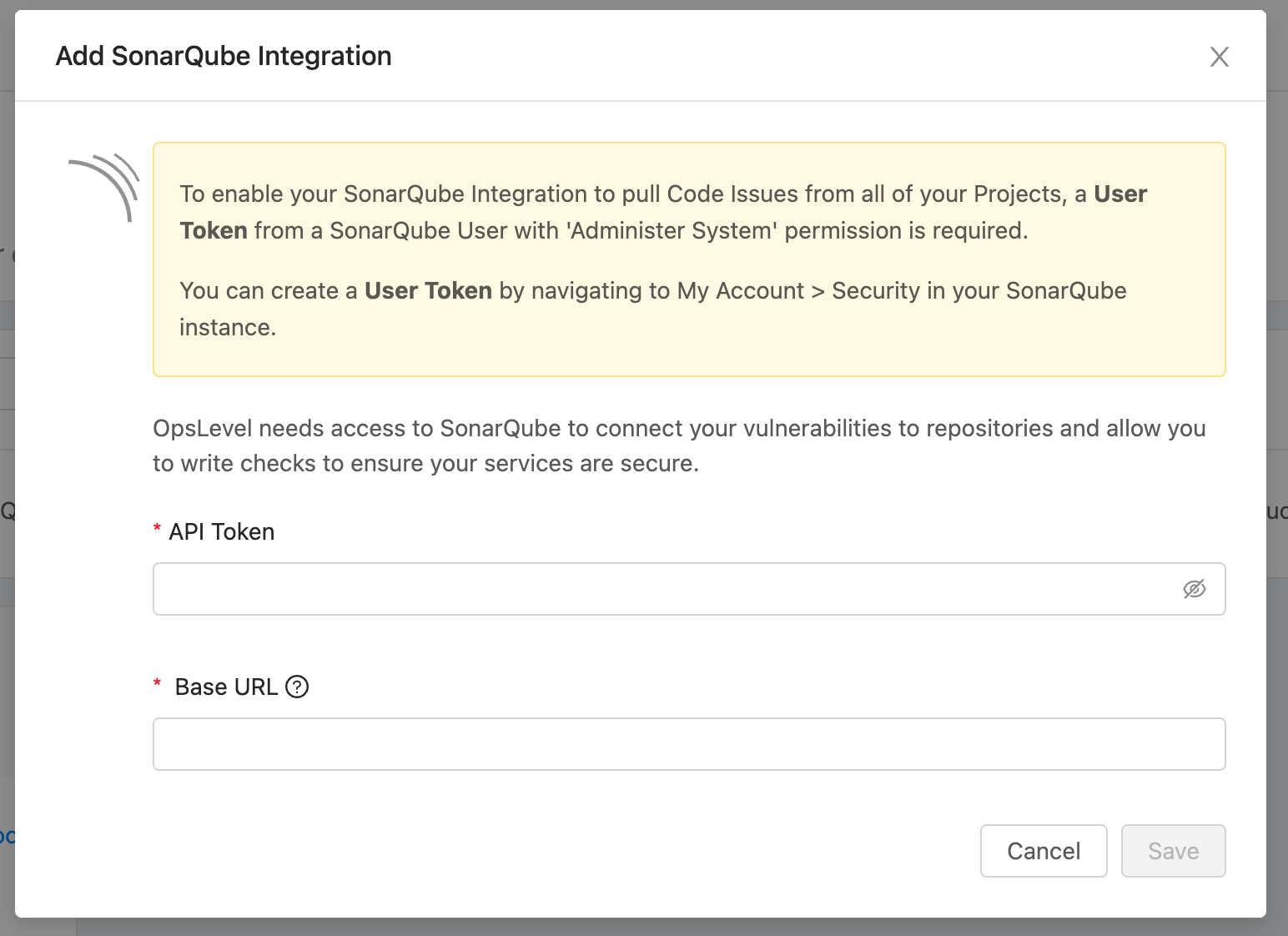
- To set up this API-based integration, you need:
- A User Account with 'Administer System' permission
- A User Token associated with that User Account
- Project or Global tokens will not work with the web API (See SonarQube Docs)
- The Base URL for your SonarQube instance (ex. https://my-sonar-install.xyz)
Associating Code Issues with OpsLevel Services
In SonarQube, Code Issues are associated with/belong to Projects or "Code Issue Projects". OpsLevel utilizes "Service Suggestions" to provide you the opportunity to link your "Code Issue Projects" to new or existing Services.
During each data sync with SonarQube, OpsLevel will pull and store each of your SonarQube Projects. When any new Projects are imported, "Service Suggestions" are created which will allow you to attach your Projects (and thus your Code Issues for that Project) to a particular Service.
- If a Service exists with the same name as your SonarQube Project, a "Service Suggestion" will be created which encourages you to link the "Code Issue Project" with the existing Service.
- If a Service with the same name does not exist, a "Service Suggestion" will be created which encourages you to create a new service and to link it to the "Code Issue Project".
"Service Suggestions" can be found under "Catalog" > "Detected "Services" in your OpsLevel dashboard.
Create a Code Issues check
With the SonarQube integration, OpsLevel stores all code issues detected by SonarQube, such as vulnerabilities and config issues, in your catalog. You can run checks against your code issues using a Code Issue Check.
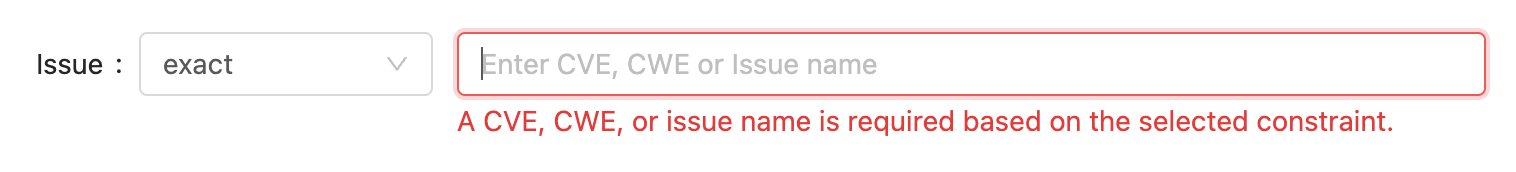
If you're checking for a specific CVE or CWE you can search for an exact match on the issue identifier.
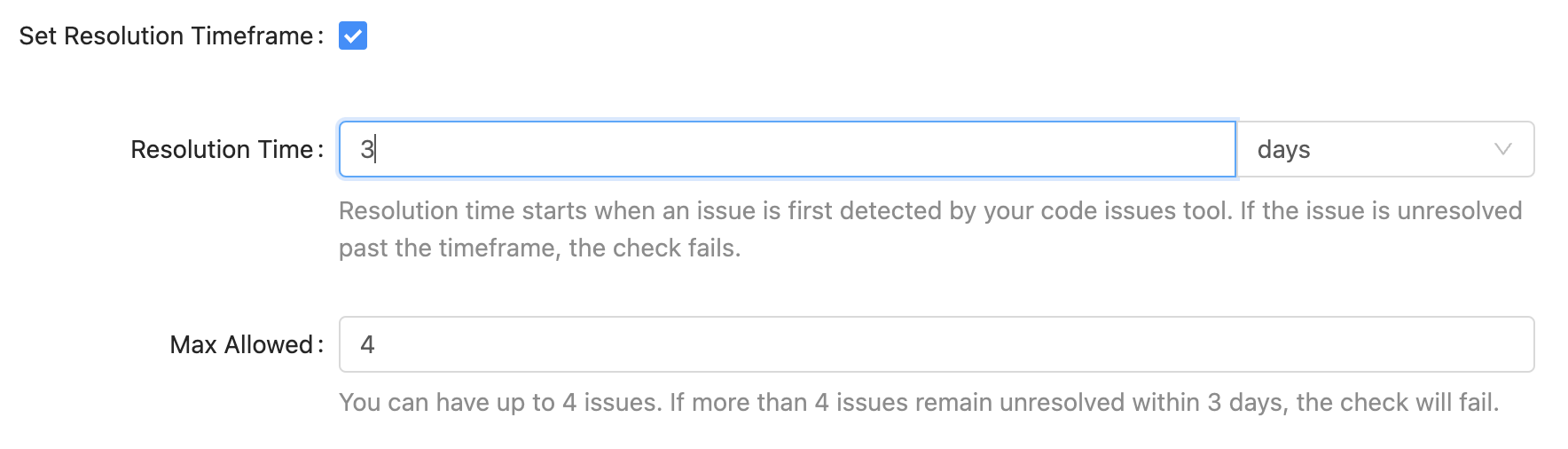
For all code issue checks, you can set a resolution timeframe, and a maximum allowable number of code issues. Your check will begin to fail if the time between a code issue being detected and the code issue being fixed exceeds that timeframe for more than the maximum allowable number of issues.
Note: Users of SonarQube v10.3 and lower will see different values for Code Issue severities and types due to a fundamental change in the way SonarQube handles these two fields since v10.4+. The functionality is identical, only the possible values should be different.
Below is a list of the old SonarQube values and their roughly similar new SonarQube value alignments:
| <10.4 Severity | 10.4+ Severity | <10.4 Type | 10.4+ Type |
|---|---|---|---|
| BLOCKER | HIGH | CODE_SMELL | MAINTAINABILITY \ |
| CRITICAL | HIGH | BUG | RELIABILITY |
| MAJOR | HIGH \ | MEDIUM | VULNERABILITY |
| MINOR | LOW | ||
| INFO | LOW |
SonarQube (legacy integration)
As of October 2024 we provide an updated, pull-based SonarQube integration. Legacy integrations continue to be supported.
Some older accounts may still have instances of our legacy integration installed, so we are including the legacy help docs below. Note that they only apply to the legacy integration.
Create a Check (legacy)
- Navigate to the Rubrics sub menu under the Service Maturity menu in OpsLevel.
- Hover over the cell that corresponds to the level and category you want your check to live in and click the + Add Check button.
- Create a SonarQube check.
- Choose one of the Check Templates from the dropdown.

Templates include:
- Check for passing Security Check: Any service whose quality gate status for
new_security_ratingmetric isERRORwill fail this check. - Check for passing Reliability Check: Any service whose quality gate status for
new_reliability_ratingmetric isERRORwill fail this check. - Check for passing Maintainability Check: Any service whose quality gate status for
new_maintainability_ratingmetric isERRORwill fail this check. - Check for passing Code Coverage Check: Any service whose quality gate status for new / updated source code is
ERRORwill fail this check.
- We will populate the Service Specifier field, which we use to determine what service to run the check for, and the Success Condition field, which we use to determine if the check should pass or fail. We also provide a sample payload to test the check.

Send payload to OpsLevel (legacy)
-
Add a new webhook for your project in SonarQube using the Webhook URL after you create the integration in the previous step
-
Ensure your SonarQube
projectKeyis configured as an alias for your desired OpsLevel service. -
Start a sonarscan to begin delivering Quality Gate information to OpsLevel. The easiest way to run a scan on demand is to use SonarQube’s docker container setup (don’t forget to set your
sonar.projectKeyinsonar-project.propertiesfirst):docker run
--rm
-e SONAR_HOST_URL="http://${SONARQUBE_URL}"
-e SONAR_LOGIN="myAuthenticationToken"
-v "${YOUR_REPO}:/usr/src"
sonarsource/sonar-scanner-cli
You can copy the SONARQUBE_URL from the SonarQube Integration page in OpsLevel.
To learn more about SonarQube, check out their getting started guide.
Updated 3 months ago
