Okta User Provisioning with SCIM
Provision users automatically from Okta to quickly build your catalog and keep your users fresh.
If your organization uses Okta to manage your employees’ access to tools and services, you can take advantage of Okta’s “Provisioning” feature to automatically grant access to OpsLevel to your users.
The integration between Okta and OpsLevel that enables this provisioning to occur is built around an industry-standard protocol known as SCIM (System for Cross-domain Identity Management). To learn more about how Okta works with SCIM, please see this article.
The remainder of this guide is focused on enabling you to configure both OpsLevel and Okta to get provisioning up and running for your organization.
If you are interested in how to set up Single Sign-On in OpsLevel via Okta, please check out our guide here.
Features
The following provisioning features are supported by OpsLevel today:
- Push Users: Users in Okta that are assigned to the OpsLevel application within Okta are automatically added as users in OpsLevel
- Update User Attributes: When user attributes are updated in Okta, they will be updated in OpsLevel.
- Deactivate Users: When users are deactivated in Okta, they will be set to ‘Deactivated’ within OpsLevel – which prevents the user from logging into OpsLevel.
- Push Groups: Push Okta Group and membership to teams in OpsLevel.
- Import Users and Groups: If OpsLevel is used as a source of truth for users and teams, Okta can import users and groups on a schedule from OpsLevel.
Requirements
SCIM-based user provisioning is available to all customers of OpsLevel at this time.
Step-by-step configuration instructions
The OpsLevel - Okta Provisioning integration uses the same Application in Okta as our Single Sign-On integration. We recommend you configure Single Sign-On first by following the steps here.
Create a SCIM Integration in OpsLevel
In order to complete Step 5, you'll need to be logged in as a user with the Admin role. For more information on roles in OpsLevel, check out the guide.
1. In the OpsLevel app, Click Integrations in the left sidebar.
2. Click the +New Integration tile.
3. On the New Integrations page, click the SCIM tile.
4. Click Create to create a new SCIM Integration.
5. On the SCIM Integration page, press the + Create API Token button and follow the prompts to create your API Token. When created, copy the token for use in Step 6 of Configuring the OpsLevel Okta Application below.
NOTE: Ensure that you keep the token in a safe place as you will need it when configuring the integration within Okta and you will not be able to retrieve the value again later. If you do need to retrieve the value you will have to replace the token by clicking Delete API Token and repeat the API Token creation flow.
6. While on this page, copy the SCIM API URL for use in Step 5 of configuring the OpsLevel application in Okta.
Configure User Provisioning in the OpsLevel Okta Application
The below steps assume you've installed the OpsLevel application in Okta already. If you haven't, follow the steps in our Single Sign-On guide for Okta.
1. In Okta, navigate to the Applications tab, then find and navigate to the OpsLevel application.
2. Click on the Provisioning tab, then click Integration in the Settings panel on the left side.
3. Click the Configure API Integration button.
4. Check the Enable API Integration checkbox to view additional settings.
5. Paste the values that were saved during configuration of the SCIM Integration in OpsLevel:
- Use the SCIM API URL (from Step 6 above) for the Base Url field.
- Use the API Token (from Step 5 above) for the API Token field.
6. Now that the Integration Settings are complete, click the To App Settings option in the left panel of the Provisioning tab and click Edit.
7. Check each box for OpsLevel's supported provisioning features:
- Create Users
- Update User Attributes
- Deactivate Users
8. Click Save.
9. Navigate to the Sign-On tab and click Edit.
10. Under Credential Details, select Email as the Application username format and click Save.
Now that provisioning is configured, you can assign your Okta users to the OpsLevel application as needed. New OpsLevel users provisioned this way will be automatically invited to your OpsLevel organization and receive a welcome email with a link to the OpsLevel application. For more information about how to assign Okta users, see Okta's documentation.
Configure Group Provisioning
1. Ensure you have first provisioned the users and/or groups in the Provisioning tab first. Provisioning will sync users into OpsLevel. You can choose to provision users individually, or provision the users in Groups. This does not provision the Groups & Group Memberships however.
2. To Provision Groups, navigate to the Group Push tab in the OpsLevel App in Okta.
3. Click the Push Groups button, and begin pushing groups by name, or rule:
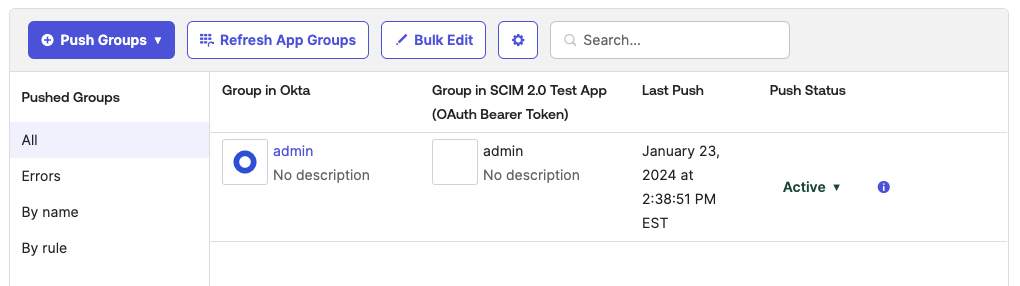
4. Done! The Okta Groups will begin syncing to OpsLevel Teams. You can check on the status in the Push Groups tab as well:
Troubleshooting
If you have questions or difficulties with the SCIM integration, hit us up at [email protected].
Updated 3 months ago
