GitLab Integration
Integrate with GitLab to perform checks against your repositories, define services through config-as-code with opslevel.yml, and view API Docs.
GitLab SaaS
Setup
OpsLevel uses OAuth to authenticate this integration. Setup is simple:
In the sidebar of your OpsLevel account, navigate to Integrations > Add New Integration Select GitLab SaaS from the list of integrations.
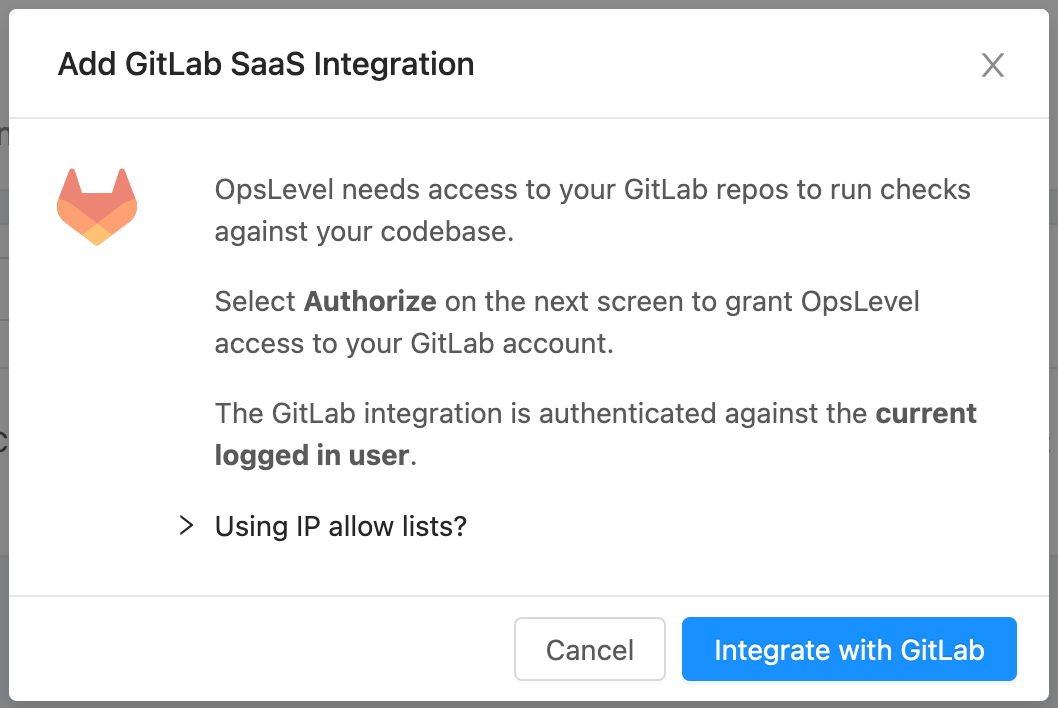
Follow the prompts from the setup wizard. A dialog box will appear and you will need to click the blue "Integrate with GitLab" button. The next dialog box will explain what OpsLevel will request access to from your GitLab account. You will need to select "Authorize OpsLevel" to complete the integration setup.
Integration Settings
Service Detection (Recommended)
You have the option to discover new services and new service metadata through GitLab. These discovered services will appear on the Detected Services page in your OpsLevel account.
Rules may be written in regular expression format to exclude certain repos from this discovery process.
Package Version Collection (Recommended)
You have the option to pull in package manager information into OpsLevel from your connected repos. These packages will import automatically if this setting is enabled, and appear under Catalog > Packages in the sidebar navigation. These can be used to write package version checks, which will automatically verify that services use (or do not use) certain software packages, and check for specific package versions.
Permissions/Scopes
The OpsLevel GitLab Integration requires at least Maintainer access to the desired Gitlab Group, but works best with Owner access. We requires the following Gitlab API scopes:
| Scopes | OpsLevel Usage |
|---|---|
| read_user | Inspect permissions |
| api | API write permissions. Only used to write webhooks |
| read_api | Used to read repository metadata, such as default branch and branch protection |
| read_repository | Used to clone repos for Git grep checks, repository analysis, etc |
| write_repository | Used to create new projects (repositories) with our service templates feature |
Gitlab self-managed
As an alternative to using the cloud-based version of GitLab, OpsLevel supports integrating with your GitLab self-managed instance to unlock the same functionality we provide through our other git integrations.
OpsLevel supports two methods to authenticate our GitLab integration:
- OAuth Application
- Personal Access Tokens
Authenticating with an OAuth Application
Set up an application in GitLab
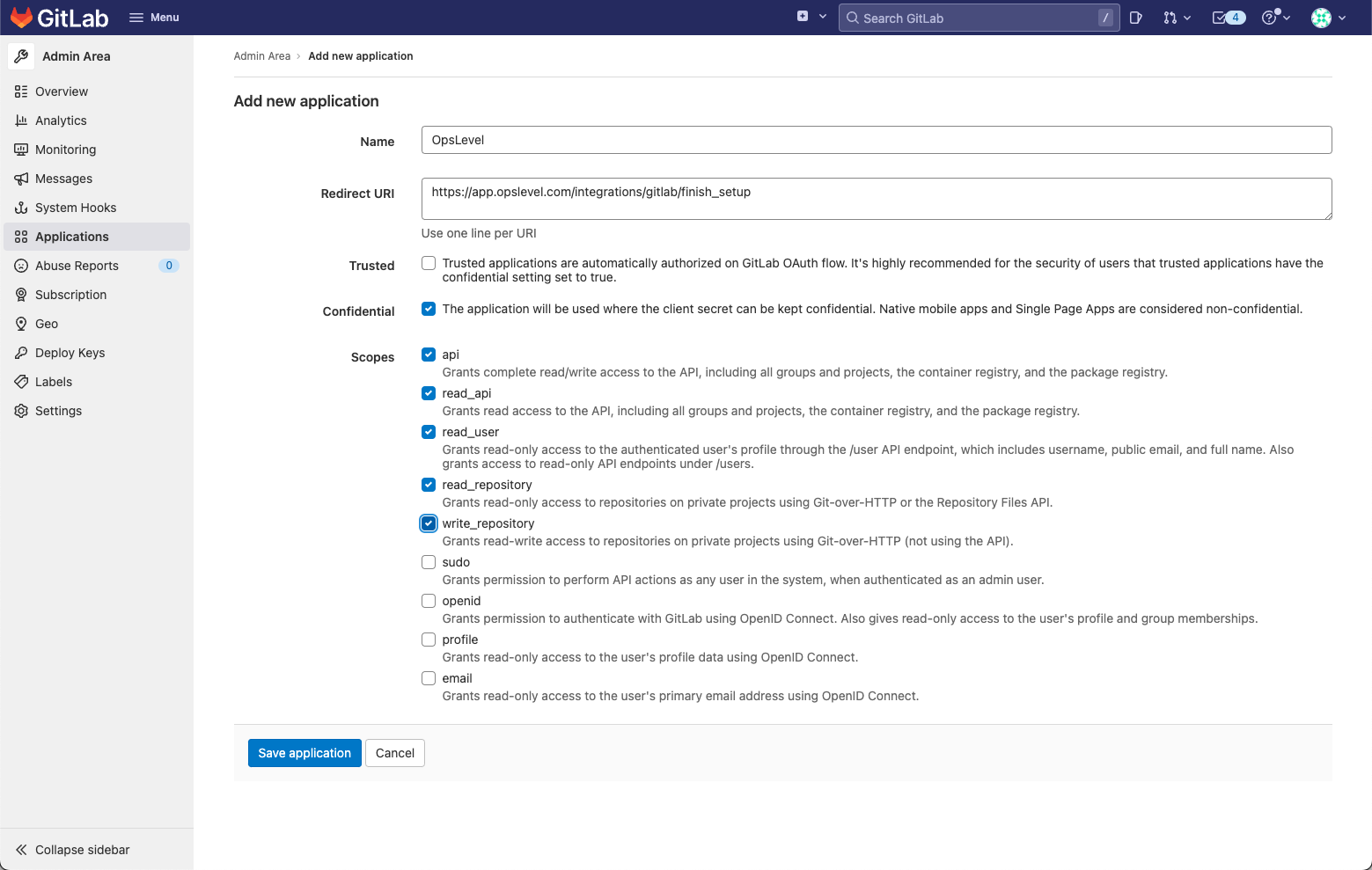
In order to integrate with OpsLevel, an administrator on your GitLab instance will need to configure an application which will allow OpsLevel to communicate with GitLab. Please refer to the instance-wide applications section for your version of GitLab for more information. Below is the typical setup of an application, alongside the OpsLevel specific values required by the application:
Note : OpsLevel supports repository integrations with GitLab versions 16.11+
- Enter OpsLevel for the application name.
- Enter https://app.opslevel.com/integrations/gitlab/finish_setup for the Redirect URI.
- OpsLevel uses several scopes to setup webhooks for your projects and query repository information. Enable these scopes:
- api
- read_user
- read_api
- read_repository
- write_repository
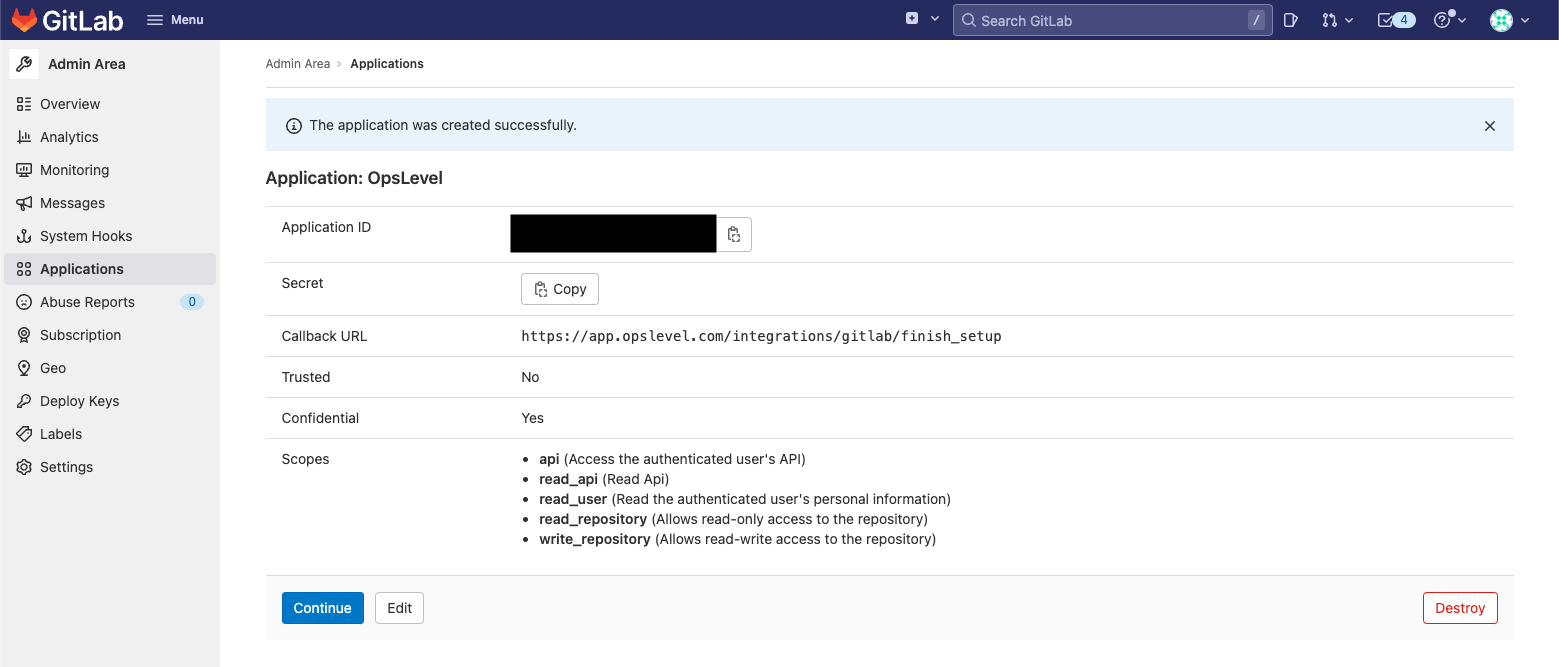
- After creating the application you should take note of the Application ID and Secret. You will need these fields when setting up the integration in OpsLevel.
Add a GitLab self-managed integration in OpsLevel
Once the GitLab application has been configured, you will be able to integrate your OpsLevel account with your GitLab self-managed instance by:
- In the OpsLevel app, clicking Integrations in the left sidebar.
- Clicking on the + New Integration button.
- Clicking the GitLab self-managed integration card.
- In the modal, entering the Application ID and Secret from the application that was created in GitLab and entering the publicly routable URL to your GitLab self-managed instance for the Base URL.

- Clicking Integrate with GitLab
Integrating Multiple Groups: If you have already integrated a group for your GitLab self-managed instance and want to integrate another one, follow the steps above to add the integration in OpsLevel. We will prefill the fields in the install modal, so you will just need to click Integrate with GitLab and select the group you want to integrate.
Authenticating with a Personal Access Token
Set up a Personal Access Token in GitLab
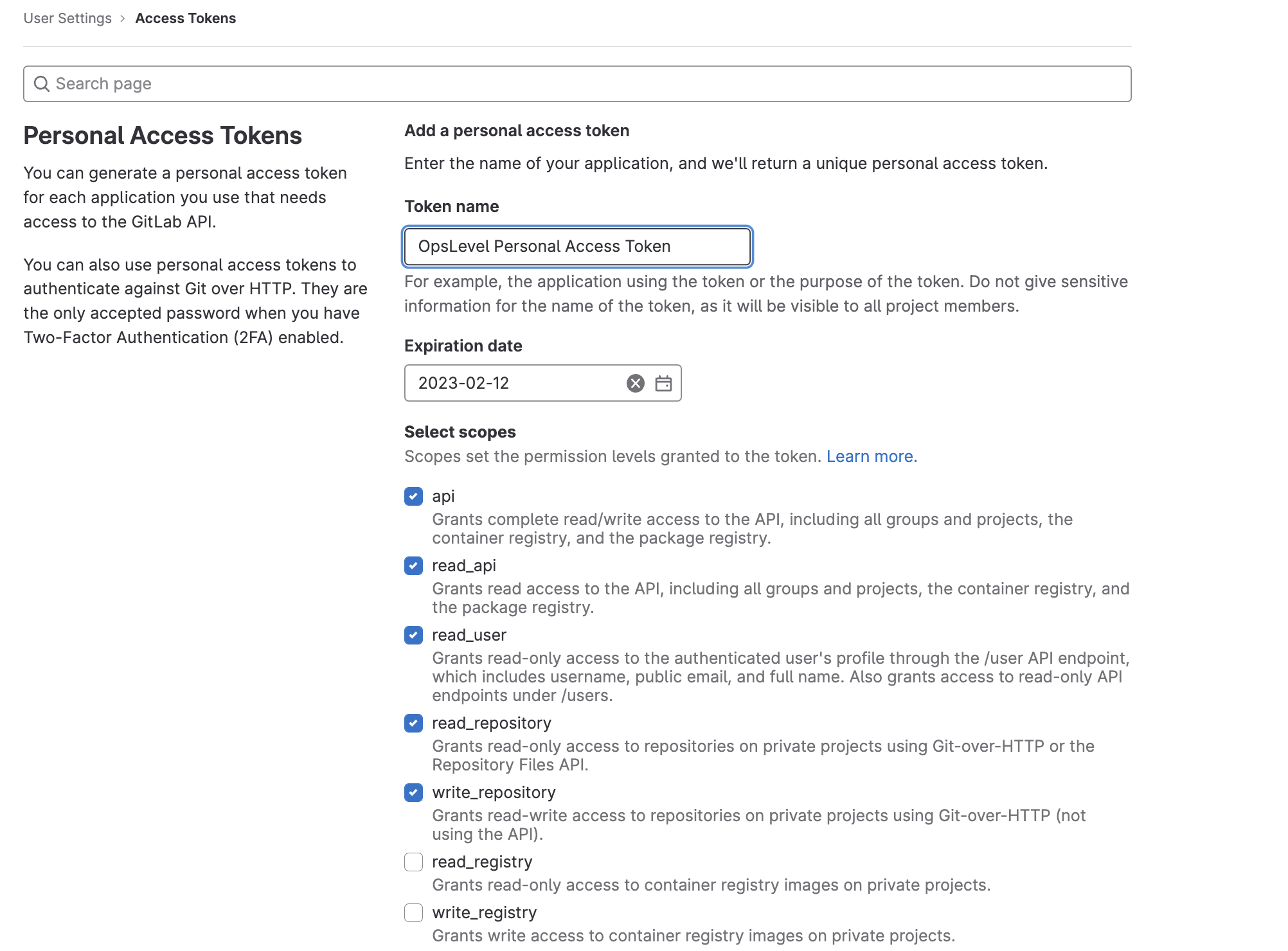
In order to integrate with OpsLevel using a Personal Access Token, you'll need to configure a Personal Access Token within GitLab. Ensure that you have at least Maintainer access to your desired Gitlab Group, but Owner access is better.
Note : OpsLevel supports repository integrations with GitLab versions 16.11+
- Enter a name for your Personal Access Token, such as "OpsLevel PAT" (Please note that the name of the PAT is going to be used when configuring the integration in OpsLevel as well).
- OpsLevel uses several scopes to setup webhooks for your projects and query repository information. Enable these scopes:
- api
- read_user
- read_api
- read_repository
- write_repository
Add a GitLab self-managed integration in OpsLevel
Once you have the PAT from GitLab, you will be able to integrate your OpsLevel account with your GitLab self-managed instance by:
- In the OpsLevel app, clicking Integrations in the left sidebar.
- Clicking on the + New Integration button.
- Clicking the GitLab self-managed integration card.
- In the modal, entering the Token Name and Access Token from the PAT that was created in GitLab and entering the publicly routable URL to your GitLab self-managed instance for the Base URL.
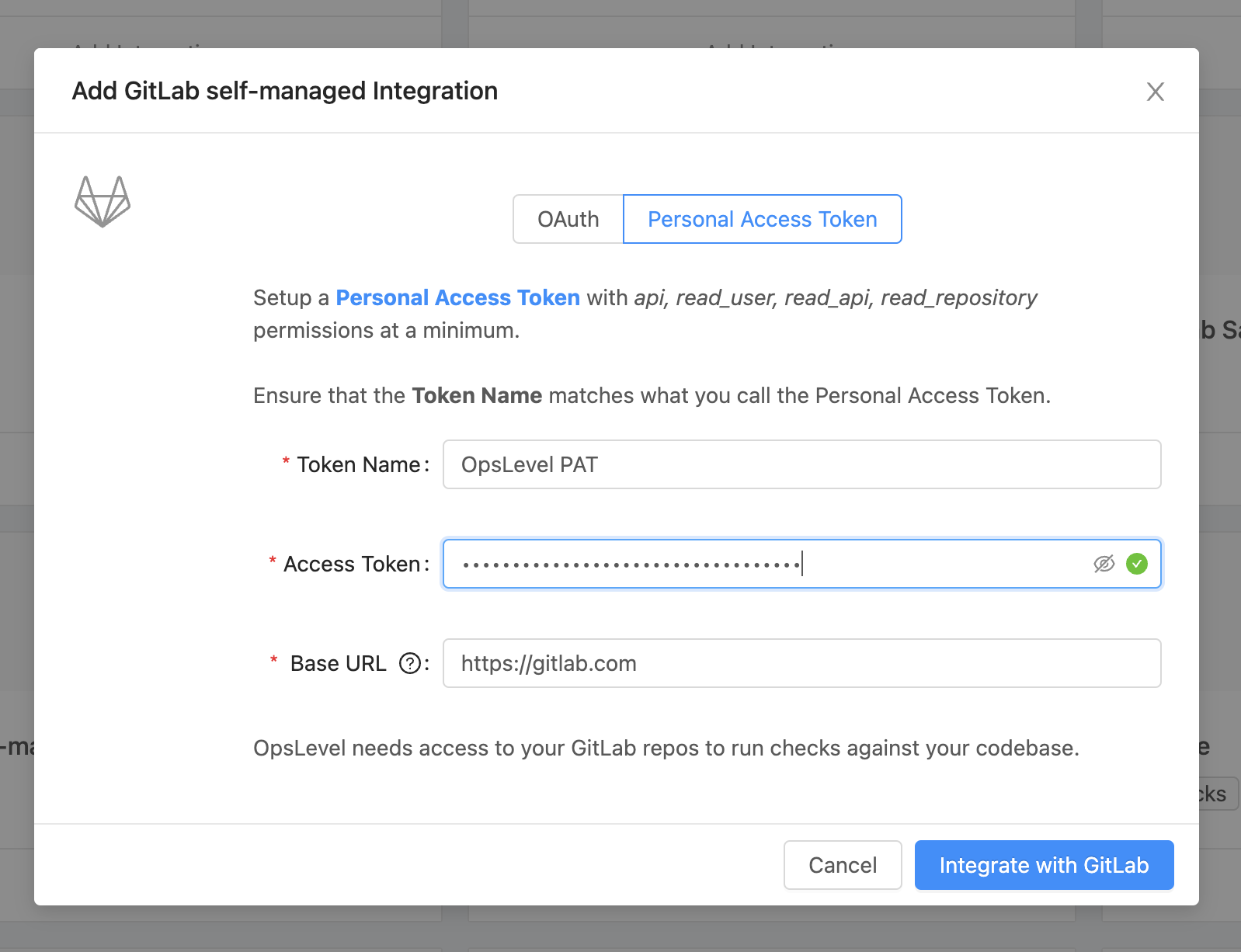
- Clicking Integrate with GitLab
Integrating Multiple Groups: If you have already integrated a group for your GitLab self-managed instance and want to integrate another one, follow the steps above to add the integration in OpsLevel. We will prefill the fields in the install modal, so you will just need to click Integrate with GitLab and select the group you want to integrate.
If you have any questions or feedback, let us know at [email protected].
Updated 3 months ago
